Technology changes at a rate most businesses can’t keep pace with, and this lag introduces considerable risk to a company’s business operations. To manage this risk, many security leaders must wade into an ever-changing, turbulent network landscape and seek to establish some order through their selected security frameworks and controls. These security leaders also apply best-practice approaches to this diverse risk portfolio using traditional concepts such as zero-trust and layered security technologies and services.
I believe this approach needs to change, especially for SMBs. This approach was created for centralized, managed networks that many of us in security first started our careers with years ago. Today’s networks typically don’t have fully defined perimeters. They are designed for the mobile worker and geo-dispersed teams with numerous third-party connections to vendors and trusted partners. It’s these new network infrastructures that exist in the cloud, in shared data centers, and on mobile devices that force SMBs and their security managers to reevaluate plans for how to implement and manage the business’s cybersecurity program without impeding new business opportunities.
Strategic plans, in essence, are cybersecurity roadmaps that establish the pathways a security manager will follow to mature their risk management approach while protecting their company. These plans should describe how the security program will preserve and share information, counter new and evolving threats, and support the integration of cybersecurity as a best practice for everyday business operations. A strategic plan should note the “current state” of security practices and describe near-term objectives to be addressed in the next 12 months, midterm goals in the next 18-24 months, and long-term objectives over the next 36 months. The security manager and critical stakeholders usually develop this plan and it should be considered a living document. The vision, goals, and objectives of this plan should be reviewed at least annually by the security manager and the SMB’s executive leadership team, with changes incorporated and new initiatives scheduled accordingly.
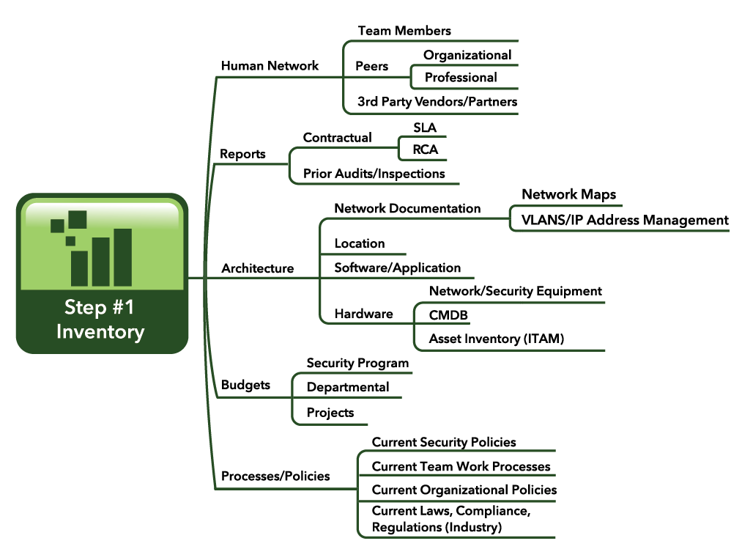
To begin, security managers must understand the current security state of their SMB. This effort will require an inventory and continuous scanning of assets such as hardware, software, network configurations, policies, security controls, prior audit findings, etc.