Cyber Crisis Response introduces the SONAR Method™, a proven, proprietary framework for responding to and managing a range of cyber incidents, from singular events to the most complex cyber breaches and crises. Crisis response is a complex undertaking that requires the coordination of multiple, often conflicting, activities. No playbook replaces experience and critical thinking. Using the SONAR Method™ will help any practitioner:
● Understand how to stabilize an environment during a cyber attack
● Learn how to organize the team and resources needed to resolve the situation
● Facilitate negotiations across a wide variety of stakeholders involved in the crisis
● Discover how to effectively articulate and communicate the situation and resolution across a multitude of stakeholders
● Develop the specific action plan required to remediate and recover from the incident
Written by experts who have lived in the trenches of response, this book describes many of the common pitfalls and their battle-tested solutions. There is no better way to learn than to do it yourself but understanding the lessons others have learned is essential to help you prepare.

Table of Contents
Cyber Crisis Response
Leveraging the SONAR Method™ to Accelerate Response and Recovery
Andrew and Chris worked together at a leading cybersecurity company. They successfully employed the concepts described in The SONAR Method™ framework to assist major clients in responding to and recovering from a cyber crisis. We organized the book into six sections, including a section to define a crisis and then the five phases according to The SONAR Method. This book reflects our experience using this method. The six sections are as follows:
Foreword by George Kurtz, Founder and CEO of Crowdstrike
Since I co-founded CrowdStrike in 2011, I have witnessed first-hand the devastating consequences that a breach can inflict on victim organizations. In recent years, high-profile breaches have sent shockwaves across every industry and serve as a wake-up call for many leaders.
As the threat landscape has become more complex and sophisticated, cyberattacks have increased with dramatic velocity. Data theft and ransomware have become commonplace, while nation-states increasingly conduct cyberespionage and misinformation campaigns to undermine democratic processes in the Western world.
At the same time, cloud-conscious adversaries increasingly target and exploit cloud environments, while the explosion of generative AI makes it easier for low-skilled adversaries to move faster and launch more ‘state-of-the-art’ attacks. Adversaries leverage stolen identity credentials and use interactive tactics with hands-on keyboard operators to evade legacy defenses. No organization is fully immune to cyberattacks. The battle is no longer about stopping malware – it’s about stopping the breach.
That’s why, since co-founding CrowdStrike, my mission has been to stop breaches and improve security outcomes for our customers. While CrowdStrike secures tens of thousands of organizations, from small businesses to large Fortune 50 clients, many organizations still rely on legacy, out-of-date solutions that are ineffective in stopping sophisticated adversaries. Unfortunately, those organizations are hit the hardest when they experience a breach. This is why I believe that being prepared for a potential crisis is so essential.
This book distills years of experience from the trenches of cyber crisis response into a framework that organizations can use to plan for a cyber crisis proactively. Andrew and Chris have taken their decades of combined experience in breach response, remediation, and executive crisis advisory and engineered a framework to help security, technology, and business leaders better prepare to handle breaches and their aftermath.
This book also provides a unique and multidimensional perspective on responding to large-scale events. It covers topics ranging from stopping the bleeding, starting the response process on the right foot, handling investigations and recovery, managing brand reputation, and working with regulators.
I have personally worked with both authors over my career. Andrew and Chris have done a fantastic job of distilling their years of experience into a crisp guide that can be used by security technologists as well as senior executives.
If you are looking for a comprehensive crisis response guide rooted in a practical understanding of the domain and written by authors with plenty of battle scars, this book is for you. My hope is that you read this book to preemptively prepare yourself and your organization before a crisis ever materializes. However, if you find yourself knee-deep in the middle of a full-blown incident, this book will be your definitive guide to weathering the storm and recovering.
Stay secure,
George Kurtz,
Co-Founder and CEO of CrowdStrike
Section 1 – Defining a Cyber Crisis (Chapters 1-5) – defines fundamental concepts underpinning crisis response, including a cyber crisis definition and defining crisis parameters. This section also provides an overview of the threat landscape and some essential guidance for organizations that want to build crisis response capabilities.
Section 2 – Stabilize (Chapters 6-9) – shows how to stop the bleeding so you can properly activate the Crisis Response Team. This phase focuses on the initial decisions during a cyber crisis to contain an event and prevent its exacerbation in your IT environment. We discuss how to stabilize the initial chaos when a crisis event occurs and get the situation under control. However, stopping the bleeding is just the first step in the response process.
Section 3 – Organize (Chapters 10-15) – demonstrates how to organize a crisis response, including setting up technical and business teams, the role of executive management in the response process, crisis management and coordination, and response planning and execution. We conclude this phase with an overview of breach response investigations and remediation and recovery considerations.
Section 4 – Negotiate (Chapters 16-19) – reveals how to negotiate with key stakeholders, especially with conflicting priorities and activities. This section also touches on negotiation with a threat actor and aligning responses to business priorities to ensure everyone works in concert towards the same goals. In the Negotiate phase, you sit down with other leaders behind closed doors and agree on concrete actions to control the crisis.
Section 5 – Articulate (Chapters 20-25) – As part of the Articulate phase, you must communicate decisions and actions to internal stakeholders, provide clear direction, articulate roles and responsibilities, and ensure everyone is marching in the same direction. Furthermore, you must also communicate with external stakeholders where appropriate. Otherwise, a negative perception will amplify the crisis and cause your organization a Public Relations nightmare.
Section 6 – Remediate (Chapters 26-30) – The last phase in The SONAR Method framework is to remediate the compromised network and recover your systems to an operational and secure state. This part will guide you through considerations and approaches to eradicating the threat actor from the compromised network and securely recovering systems so the actor cannot easily return to continue their operations.
Note that the Remediate part of the SONAR framework is an overarching term encompassing the remediation of security weaknesses that led to a crisis, system restoration, and recovering the impacted environments to an operational state.
The framework may appear linear at first. However, you should use it iteratively and incrementally when responding to a crisis.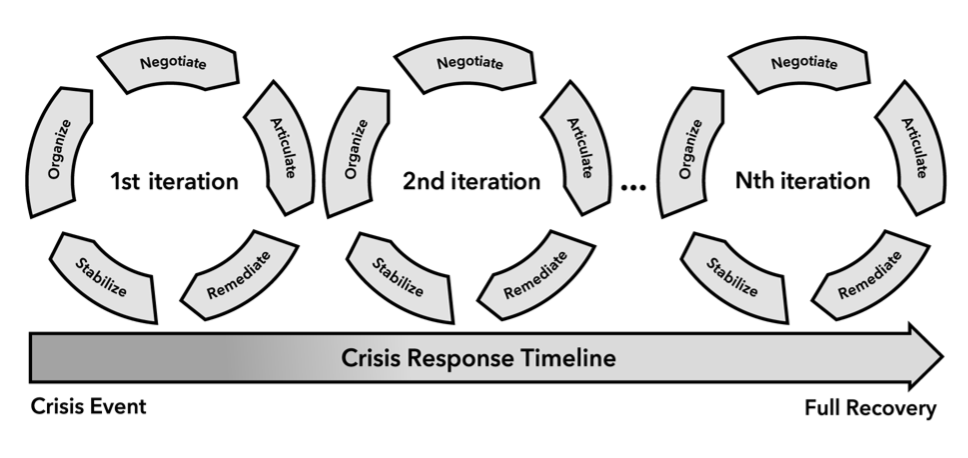
Crisis response is often a messy and convoluted process. The purpose of this framework is to provide you with a structure and guidelines to handle a cyber crisis event. However, feel free to tailor the framework to your response needs. Apply your judgment and critical thinking and leverage the framework based on your unique context.
Your content goes here. Edit or remove this text inline or in the module Content settings. You can also style every aspect of this content in the module Design settings and even apply custom CSS to this text in the module Advanced settings.
