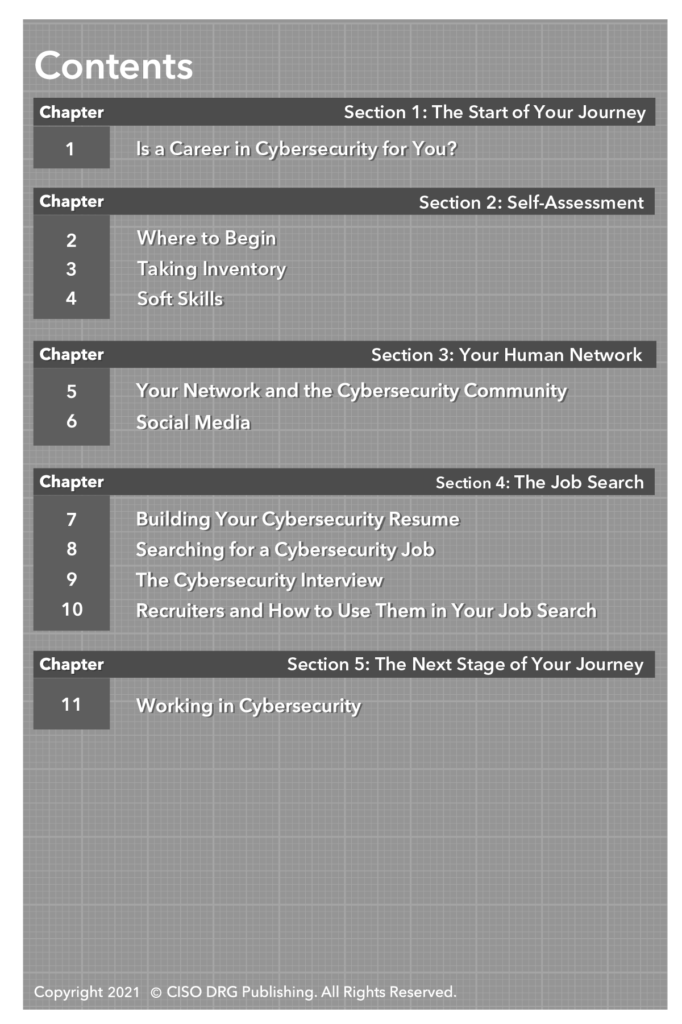
The Practitioner Series is intended for the CISO, their direct staff, and all practitioners of cybersecurity in the firm who need to understand critical processes at an in-depth level. For executives and managers who are required to lead the response to cyber crises, we offer Cyber Crisis Response: Leveraging the SONAR Method™ to Accelerate Response and Recovery. Written by crisis response experts Andrew Gorecki and Christopher Scott, this book walks you through a tried and true method develop by Andrew and Chris through their years of experience in leading companies in responding to cyber events that devolved into full-blown crises. Also in this series is Develop Your Cybersecurity Career Path, which goes in-depth about breaking into cyber at any level. Straight out of school, transitioning from a military career or doing a mid-career transition, this book is for you.
As a CISO and a leader, you are responsible for the security of your organization’s software. This book will provide best practices for implementing a Secure Development Lifecycle (SDL) in your organization. This allows you and your organization to create secure software while maximizing business value.
Our book ‘A Comprehensive Guide to Application Security for CISOs offers a unique and holistic approach that allows you to cost-effectively integrate a state-of-the-art SDL into the organization’s security program and product life cycle.
We have certainly entered the era of the celebrity breach. Rather than dwell on the technical capabilities of the bad actors or the technical shortcomings of the victims, in this book we’re going to focus on the key lessons we can learn. It is so important that everyone understands how their role contributes to the overall security of the venture, so we’ll look at the controls we should have in place, the best practices we should implement, the monitoring that would detect our vulnerabilities, and the audit tasks we should perform to create a healthier program. Board members are asking “Could this happen to us?” and we need to examine what went wrong before we can answer that question.
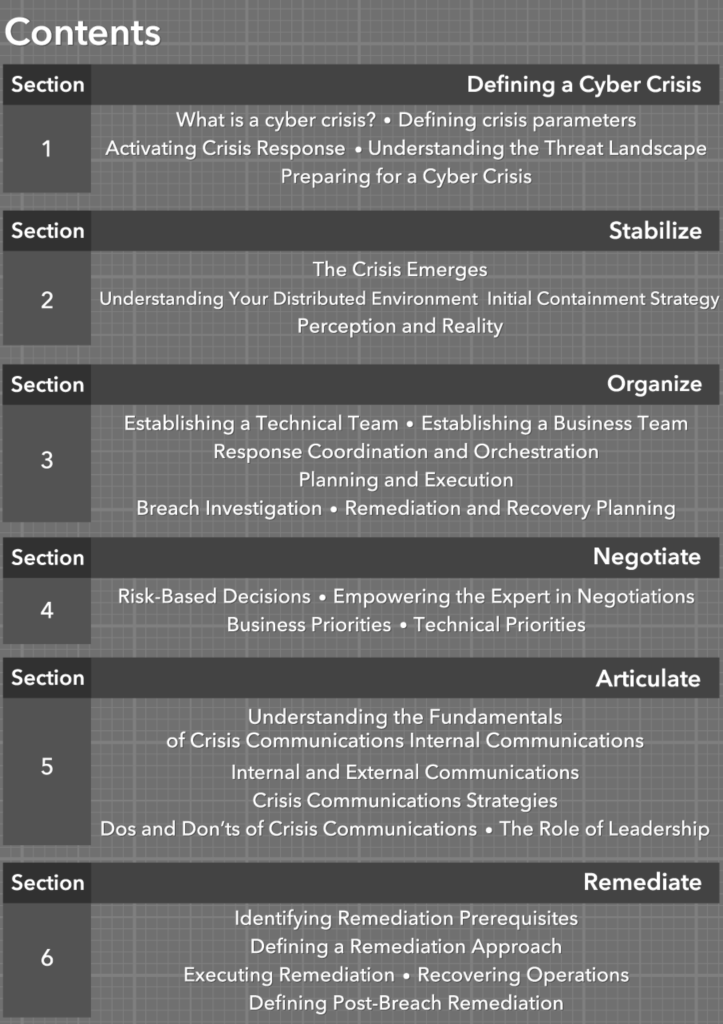
This book can be used to strengthen your team and educate executives who wish to have a deeper understanding of incident response preparation and incident postmortem investigations. It can also be used by educators as material for class assignments, including group projects.