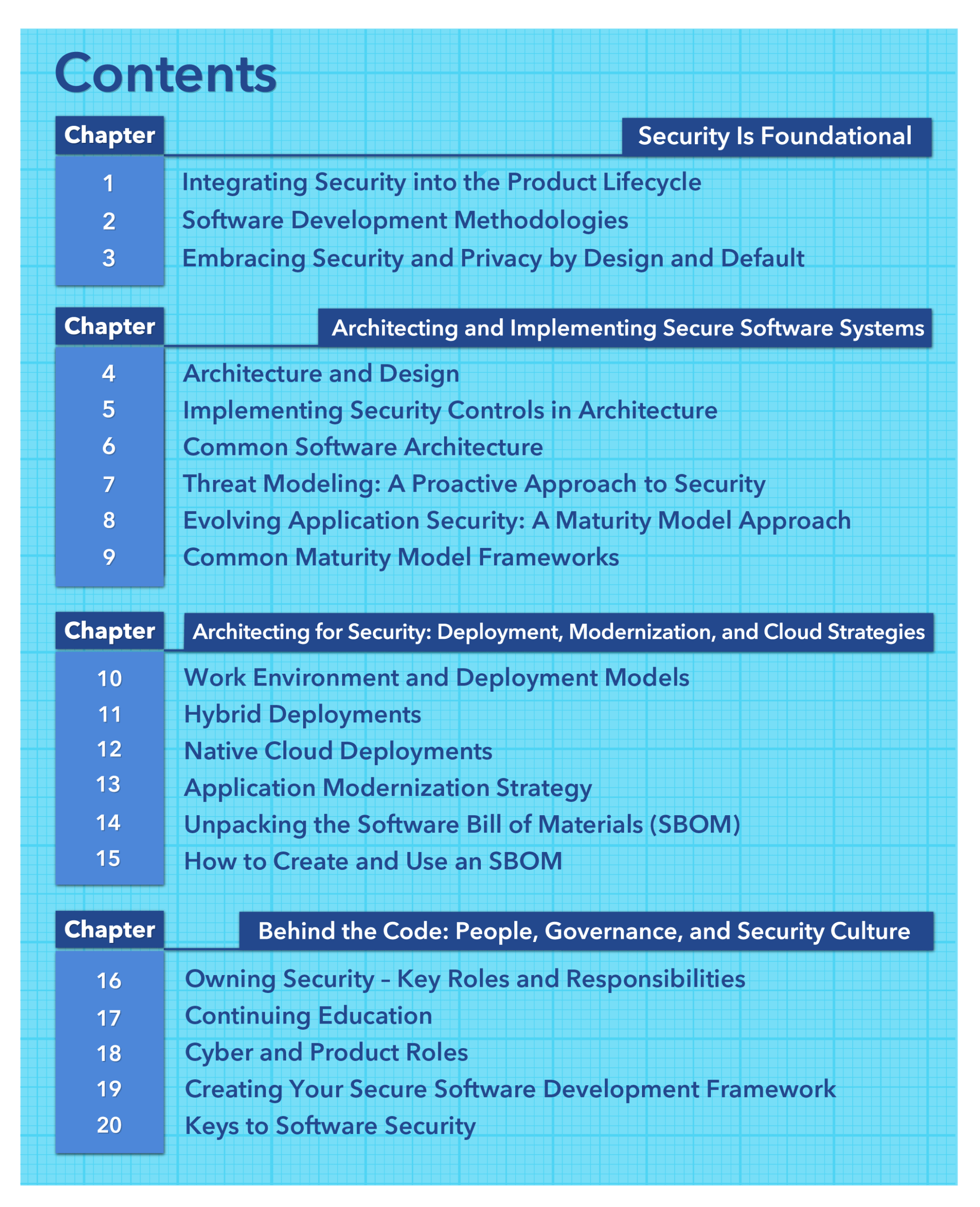
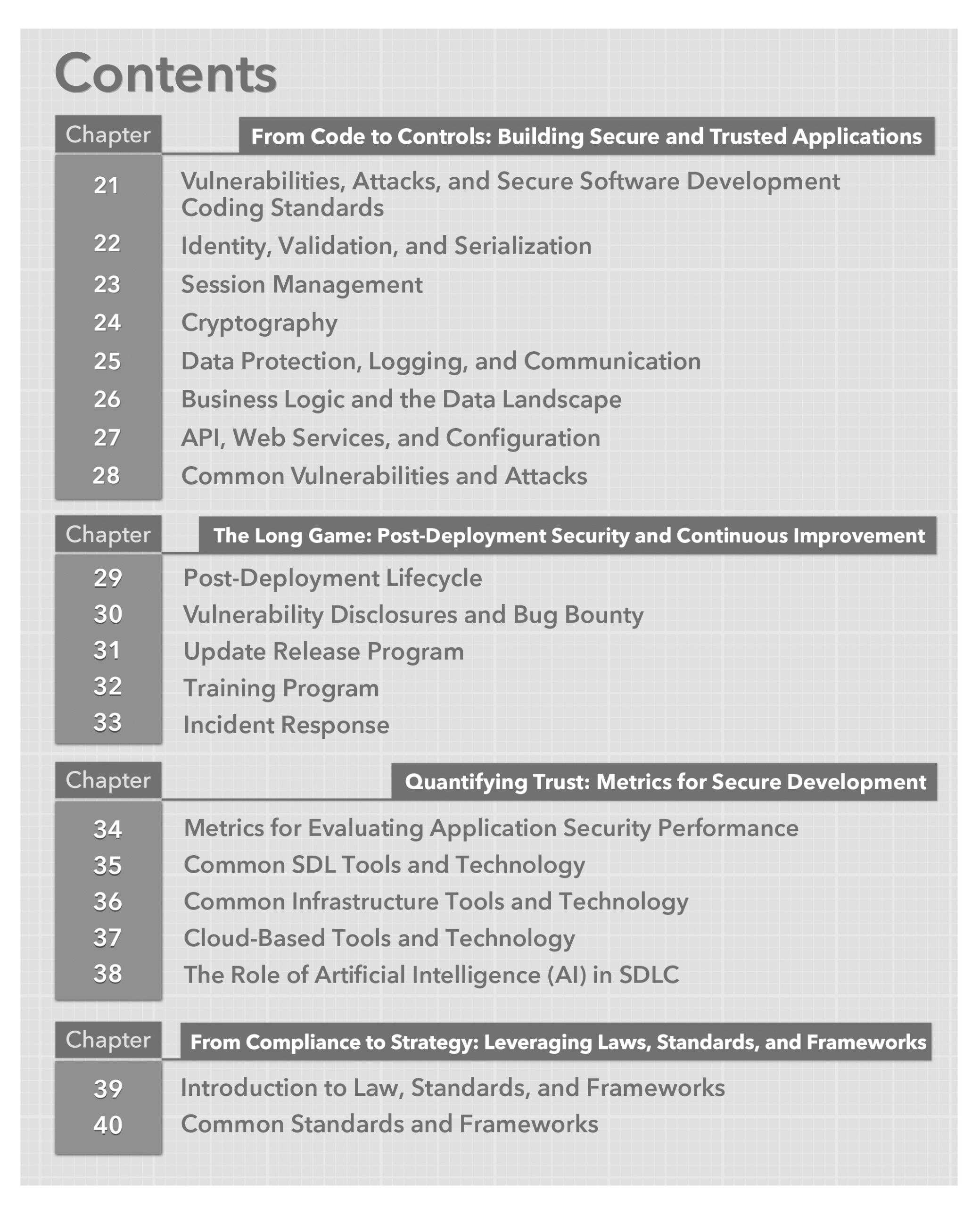
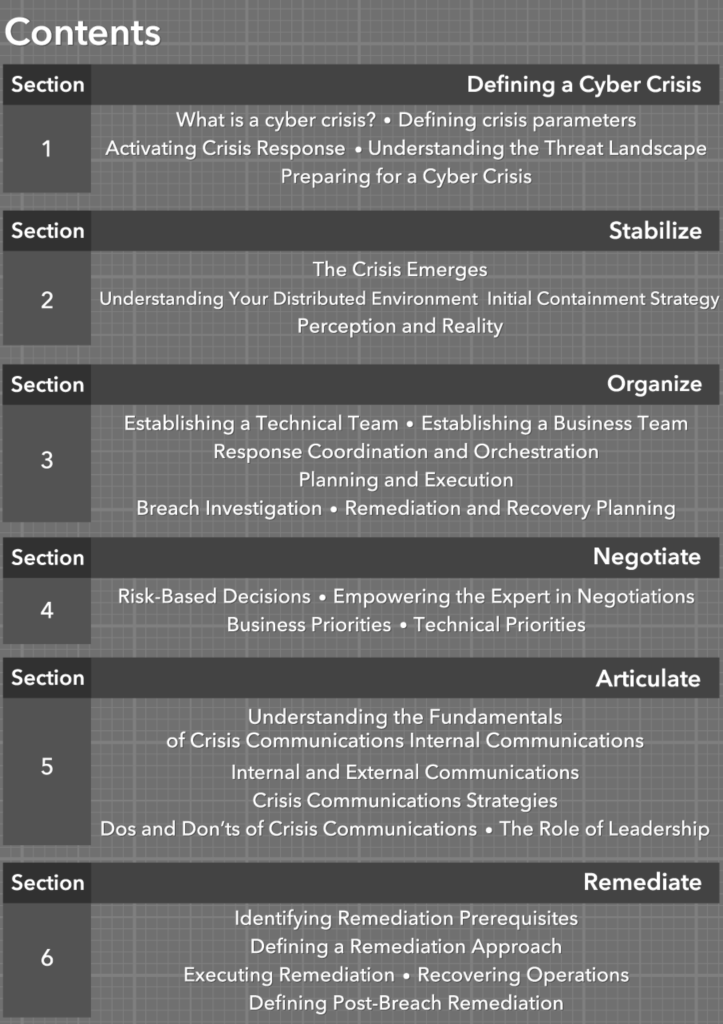
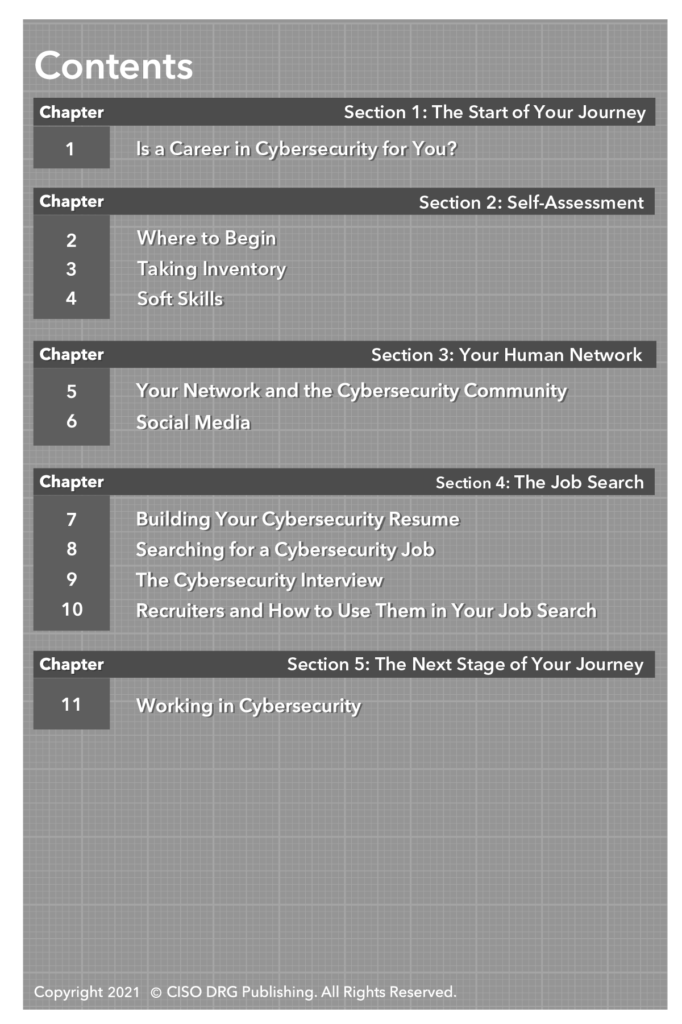
We have certainly entered the era of the celebrity breach. Rather than dwell on the technical capabilities of the bad actors or the technical shortcomings of the victims, in this book we’re going to focus on the key lessons we can learn. It is so important that everyone understands how their role contributes to the overall security of the venture, so we’ll look at the controls we should have in place, the best practices we should implement, the monitoring that would detect our vulnerabilities, and the audit tasks we should perform to create a healthier program. Board members are asking “Could this happen to us?” and we need to examine what went wrong before we can answer that question.
This book can be used to strengthen your team and educate executives who wish to have a deeper understanding of incident response preparation and incident postmortem investigations. It can also be used by educators as material for class assignments, including group projects.